Table of Contents
Introduction
Have you ever wondered how does a block of information on a blockchain gets locked? The answer lies in how each block of information is locked after it’s created. Blockchain technology, known for its decentralized and transparent nature, uses advanced cryptographic methods to ensure that once a block is locked, it cannot be tampered with. This locking process is essential for maintaining the trust and integrity of the entire network.
In simple terms, when a transaction occurs, it’s verified by multiple participants (miners or validators) and then grouped into a block. But how does this block of information get locked? Through a process involving cryptographic hashing and consensus mechanisms like Proof of Work or Proof of Stake, the block becomes part of an immutable chain. Once locked, the block is secured forever, making blockchain a highly reliable and secure technology for digital data storage.
- A list of transactions
- A timestamp
- A cryptographic hash of the previous block
The blockchain operates through a consensus mechanism, allowing multiple participants to verify and validate transactions without needing a central authority. It ensures:
- Transparency: All participants can view the transaction history.
- Immutability: Once added, blocks cannot be altered, preventing fraud.
- Decentralization: Distributed across a network of nodes, increasing security.
Blockchain’s potential applications include:
- Cryptocurrencies (e.g., Bitcoin)
- Smart contracts
- Supply chain management
Understanding blockchain facilitates exploring its various applications and implications.

The Structure of a Blockchain
A blockchain consists of multiple linked blocks, each containing vital information. Each block comprises several key components:
Header: Contains metadata such as:
- A timestamp
- The block’s unique hash
- The previous block’s hash
- Data: Contains the actual information or transactions.
- Nonce: A number needed for the cryptographic puzzle.
- Merkle Root: A hash representing all transactions.
New blocks are appended through mining. In this process:
- Miners solve complex cryptographic puzzles.
- The nonce is adjusted to find a hash below a target value.
- Once found, the block is added to the blockchain.
- This ensures integrity and security.
What Is a Block?

A block in a blockchain is essentially a digital file that stores data. It is comprised of three main elements:
- Data: This includes relevant information such as transaction details.
- Hash: A unique code that identifies a block and its contents, akin to a fingerprint.
- Previous Block’s Hash: Links the current block to the previous one, creating a chain.
Blocks are created by nodes, which are computers participating in the network. Once filled with data, a block is added to the chain in a linear, chronological order. This structure ensures transparency and security.
| Step | Description |
|---|---|
| 1. Transaction Data Creation | Users create a transaction, containing the sender, receiver, and amount of digital currency. |
| 2. Transaction Verification | Miners (or validators) verify the transaction, ensuring it meets the blockchain’s rules. |
| 3. Block Formation | Verified transactions are grouped together into a block, forming a new data set for the blockchain. |
| 4. Hash Creation | A cryptographic hash is generated for the block, acting as a digital fingerprint, unique to that block. |
| 5. Proof of Work/Stake | Miners (in Proof of Work) solve complex math problems, or validators (in Proof of Stake) are chosen to validate the block. |
| 6. Block Broadcast | The verified block is broadcast to the network, where other nodes check its validity. |
| 7. Block Locking | Once a block is validated, it is added to the blockchain, becoming part of the immutable ledger. |
| 8. Chain Linking | The block’s hash links it to the previous block, securing its position in the chain and locking its data. |
| 9. Block Finalization | After a consensus is reached, the block becomes part of the permanent blockchain and can’t be altered. |
| 10. Reward Distribution | Miners or validators receive a reward for their effort, usually in cryptocurrency. |
Components of a Block: Header and Data
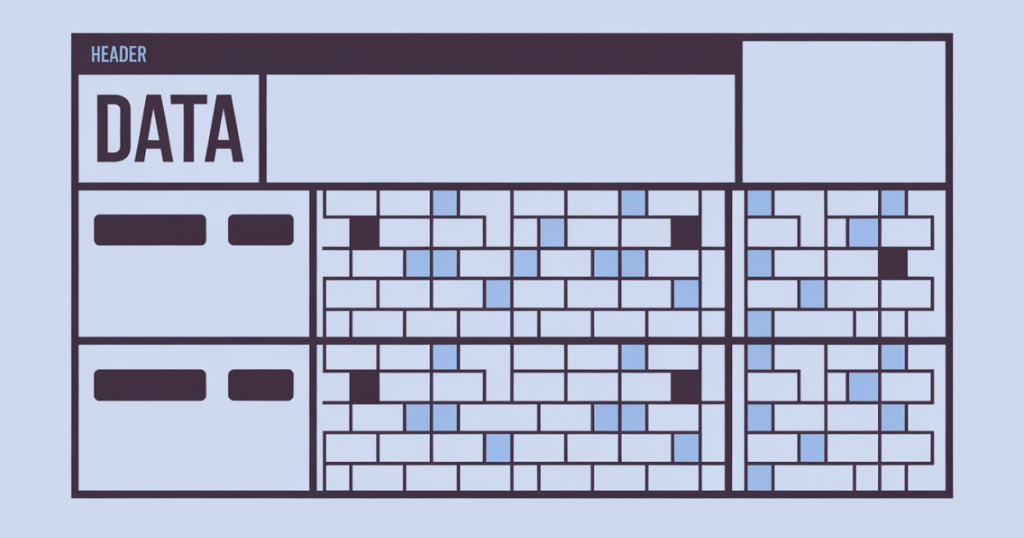
Each block in a blockchain has two primary components:
Header
- Previous Block Hash: Links the current block to the previous one.
- Timestamp: Indicates when the block was created.
- Nonce: A unique number that miners adjust to solve the block’s cryptographic puzzle.
- Merkle Root: A hash of all the transactions within the block, ensuring data integrity.
Data
Transactions: Records of the actions being processed.
- Smart Contracts: Self-executing contracts with the terms directly written into code.
- Additional Metadata: Any other necessary information relevant to the block.
The Process of Adding a Block
Adding a block involves several steps:
- Data Collection: Transactions are collected in a block, awaiting validation.
- Verification: Network nodes verify transactions using consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS).
- Hashing: Each block contains a cryptographic hash of the previous block, ensuring data integrity.
- Proof of Work: Miners solve complex mathematical problems to add the block, and verify transactions.
- Broadcast: Once solved, the new block is broadcast to the network.
- Validation: Other nodes validate the new block.
- Addition: The block gets added to the blockchain, securing the data.
Understanding Cryptographic Hash Functions
Cryptographic hash functions are integral to blockchain technology. They take input data and produce a fixed-length string, known as a hash, which appears random. Key characteristics of these functions include:
- Deterministic: The same input always results in the same hash.
- Quick Computation: Hash value is generated swiftly.
- Pre-image Resistance: Impossible to reverse-engineer the original data from the hash.
- Small Changes: Slight alterations in the input drastically change the hash.
- Collision Resistant: Unlikely to find two different inputs producing the same hash.
These properties ensure data integrity and security within blockchain systems.
Why Hashing Is Critical for Security

Hashing plays an essential role in securing blockchain data by transforming input data of any size into a fixed-size string of characters.
- Immutability: Once data is hashed, any small change in the input creates a vastly different hash, ensuring data integrity.
- Consistency: The same input will always produce the same hash, enabling verification.
- Uniqueness: Different inputs generate unique hashes, preventing duplication.
- Efficiency: Hash functions operate quickly, making real-time security feasible.
- Verification: Hash functions verify data authenticity without exposing sensitive information.
“Hashing secures data by ensuring tamper-free records and verifying transactions efficiently.”
The Concept of a Chain: How Blocks Are Linked
In blockchain technology, blocks are linked through a process known as hashing. Each block contains:
- Data: Transaction details.
- Hash: A unique identifier for the block, computed using a cryptographic hash function.
- Previous Block’s Hash: The hash of the preceding block in the chain.
The link between blocks is established via the previous block’s hash, ensuring chronological order and integrity. If a block’s data is altered, its hash changes, breaking the chain. Thus, each block serves as a tamper-evident seal, providing security and transparency. Immutable and decentralized, blockchains form an unalterable ledger.
Consensus Mechanisms: Proof of Work vs. Proof of Stake
Proof of Work (PoW)
- Miners solve complex mathematical puzzles.
- The high computational power is required.
- Secure but energy-intensive.
- Implemented in Bitcoin
Proof of Stake (PoS)
- Validators are chosen based on the number of coins they hold and are willing to “stake.”
- No need for extensive computational power.
- More energy-efficient than PoW.
- Often used in newer blockchains like Ethereum 2.0.
“Consensus mechanisms ensure that all participants agree on the current state of the blockchain.”
Why Blockchain Is Considered Secure

Blockchain’s security comes from several key factors:
- Decentralization: Information is stored across multiple nodes, reducing the risk of centralized attacks.
- Immutability: Once data is recorded, it cannot be altered without consensus from the network.
- Encryption: Data is secured using complex cryptographic algorithms, making it difficult to hack.
- Consensus Mechanisms: Protocols like Proof of Work (PoW) or Proof of Stake (PoS) ensure that all network participants agree on the validity of transactions.
- Transparency: Transactions are visible to all participants, promoting trust and accountability.
- Redundancy: Multiple copies of the blockchain exist, providing data resilience.
Potential Vulnerabilities and Mitigations
Blockchain is not entirely immune to vulnerabilities. Distributed Denial of Service (DDoS) attacks, Sybil attacks, and 51% of attacks are potential threats.
- DDoS Attacks: Overloading the network with traffic can disrupt operations. Mitigation includes using robust, decentralized networks and advanced DDoS protection services.
- Sybil Attacks: Malicious entities create multiple fake identities. Mitigation involves integrating identity verification mechanisms and deploying effective reputation systems.
- 51% Attacks: Control over the majority of the network’s mining power can lead to manipulation. Mitigation entails increasing network nodes and supporting diverse, decentralized mining pools.
Real-World Applications of Blockchain
- Finance: Blockchain powers cryptocurrencies like Bitcoin and enables transparent transactions, reducing the need for intermediaries.
- Supply Chain: It ensures product authenticity and traceability from origin to consumer, reducing fraud and enhancing efficiency.
- Healthcare: Secures patient data, allowing seamless sharing among authorized parties while maintaining privacy and integrity.
- Voting: Provides a transparent and tamper-proof system for casting and counting votes, ensuring election integrity.
- Smart Contracts: Automates contract execution, leading to reduced costs and elimination of errors.
- Identity Verification: Enhances security through immutable records, reducing the risk of identity theft.
- Real Estate: Streamlines property transactions and ownership transfers, reducing paperwork and fraud.
Future Trends in Blockchain Technology
Blockchain technology is continually evolving, with several emerging trends set to shape its future:
- Interoperability: Focus on connecting different blockchain networks.
- Scalability Solutions: Implementing sharding and off-chain transactions.
- Energy Efficiency: Exploring energy-efficient consensus mechanisms.
- Enhanced Security: Using quantum-resistant cryptography.
- Decentralized Finance (DeFi): Expanding use cases beyond traditional finance.
- Regulatory Compliance: Developing frameworks for legal clarity.
- NFTs and Digital Assets: Innovating beyond art into real estate and intellectual property.
- Blockchain-as-a-Service (BaaS): Simplifying adoption for enterprises.
- Integration with IoT: Enabling secure, automated systems.
What is the Purpose of Blockchain Technology?
Blockchain technology aims to create a decentralized and transparent system for recording transactions and data. Below are the primary purposes:
- Decentralization: Removes the need for a central authority by distributing data across multiple nodes.
- Transparency: Offers an open ledger where all participants can view transactions.
- Security: Utilizes cryptographic techniques to secure data and prevent tampering.
- Immutability: Ensures that recorded data cannot be altered or deleted.
- Efficiency: Streamlines processes, reducing the need for intermediaries.
- Cost Reduction: Lowers costs by eliminating third parties and automating transactions.
How Does a Hash Help Secure Blockchain Technology?
A hash functions as a critical security feature in blockchain technology by generating a unique identifier for each block of information.
- Data Integrity: Hashes validate that the data within a block has not been altered. Any minor change in the input data produces a completely different hash.
- Linking Blocks: Each block contains the hash of the previous block, forming a chain. This linkage ensures that modifying one block would alter subsequent blocks, revealing tampering instantly.
- Proof of Work: Hash functions are integral to the Proof of Work consensus mechanism, requiring miners to solve complex mathematical problems to add blocks, preventing malicious attacks.
FAQS
What does it mean when a block is “locked” on the blockchain?
When a block is “locked,” it means the information inside it has been approved and added to the blockchain permanently. Once locked, it can’t be changed or messed with.
How does a block get approved before being locked?
The block goes through a process where special computers or people (called miners or validators) check if the information is correct. Once they agree, the block is locked into the chain.
What keeps the block secure once it’s locked?
Each block is given a unique code (called a hash) that acts like a fingerprint. If anyone tries to change the block, the code will change too, showing that something is wrong, which keeps the block safe.
How are the blocks connected?
Each block has the code (hash) of the previous block inside it, linking them together. This chain of blocks makes it hard for anyone to change a block because it would break the whole chain.
What happens after a block is locked?
Once locked, the block is shared with everyone in the blockchain network, so everyone has the same copy. This makes the information open to everyone and prevents it from being changed.
Conclusion:
Blockchains offer unparalleled security by making data tampering virtually impossible. Their decentralized nature ensures transparency across multiple nodes. Smart contracts automate processes, eliminating intermediaries and reducing costs. Industries from finance to healthcare benefit from improved traceability and accountability. Cryptographic algorithms protect user privacy and data integrity.
Key Points:
- Decentralization: Eliminates single points of failure.
- Security: Uses cryptographic techniques to secure data.
- Transparency: Every transaction is recorded and open for verification.
- Automation: Smart contracts streamline processes.
- Efficiency: Reduces the need for intermediaries.
Blockchains are revolutionizing how information is stored and verified.

